Blockchain technology, renowned for its decentralized and secure nature, is susceptible to a threat known as the 51% attack, particularly in private blockchain networks. In this discourse, we will delve into the intricacies of 51% attacks, their implications, and effective strategies to mitigate such threats within private blockchains.
What is a 51% Attack?
A 51% attack transpires when a single entity or a group of colluding entities amass more than 50% of the computational power (hash rate) within a blockchain network. This dominance enables them to control the network, potentially allowing malicious activities such as doublespending, halting transactions, or even modifying transaction history.
Implications of 51% Attacks in Private Blockchains
While public blockchains like Bitcoin are more resilient to 51% attacks due to their widespread participation and computational power, private blockchains are inherently more vulnerable. In a private blockchain network, the number of participating nodes and their computational power is limited, making it easier for a malicious actor to achieve majority control.
The ramifications of a successful 51% attack on a private blockchain can be severe:
- Doublespending: The attacker can spend the same cryptocurrency units multiple times, undermining the integrity of transactions.
- Transaction Reversals: By controlling the majority of the network, the attacker can reverse transactions, leading to chaos and distrust among participants.
- Network Halting: The attacker can halt all transactions within the network, causing disruptions to legitimate operations.
- Loss of Credibility: Such attacks tarnish the reputation of the blockchain network, leading to loss of trust among users and stakeholders.
Mitigation Strategies
Despite the inherent vulnerabilities, there are several strategies that private blockchain networks can employ to mitigate the risk of 51% attacks:
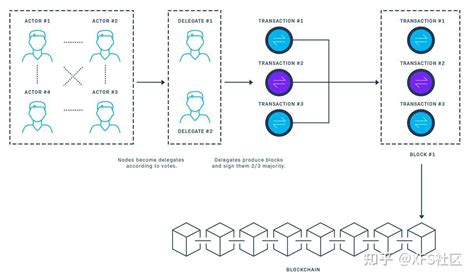
Conclusion
In conclusion, 51% attacks pose a significant threat to the integrity and security of private blockchain networks. However, with proactive measures and strategic implementation of mitigation strategies, organizations can effectively safeguard their blockchain ecosystems against such malicious activities. By prioritizing network resilience, collaboration, and technological innovation, the potential impact of 51% attacks can be mitigated, ensuring the continued viability and trustworthiness of private blockchain networks.
标签: 区块链 51攻击 区块链私有链是什么意思 区块链私链搭建







